Despite its public shutdown, crypto mixer eXch appears to be still involved in laundering operations, with analysts identifying its mixed-pool model as a key risk for compliance.
Crypto mixing service eXch, which gained a reputation for its involvement in laundering millions in stolen funds from Bybit, seems to remain active behind the scenes despite its public shutdown in late April.
Analysts at a blockchain forensic firm TRM Labs explained in a recent report that eXch continues to provide application programming interface access to its business partners, including mixers and privacy services. TRM has observed on-chain activity that suggests ongoing laundering behaviors, especially tied to its mixed-pool infrastructure.
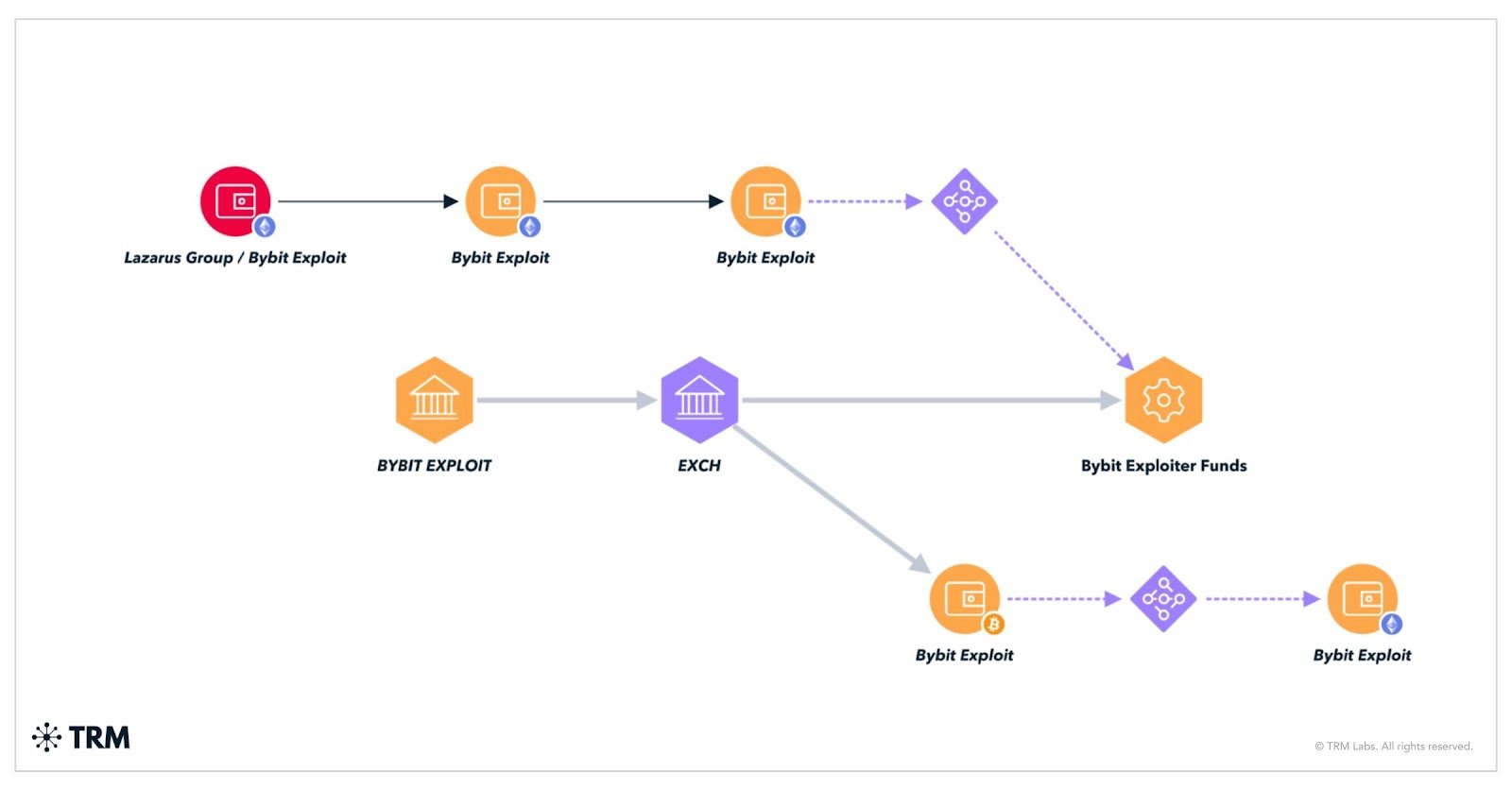
The analysts have linked eXch to significant criminal activity, including a long-term association with child abuse material threat actors.
“We have identified that eXch has been directly exposed to more than $300,000 in CSAM-related funds. However, we expect this figure to increase as we continue our attribution on eXch.”
TRM Labs
The exchange’s mixed-pool mechanism, designed to fragment transactions, has raised red flags for investigators. TRM Labs explained that in a mixed pool “all received and sent transactions are mixed together and there is no way to discover how many people are behind certain addresses and traceability is extremely difficult.” This lack of transparency complicates risk assessments, as illicit deposits may be linked to legitimate withdrawals, the analysts added.
Crypto mixer eXch announced its official shutdown on April 17. However, the protocol removed the message a few hours later — leaving “no public record of its communication on this topic,” and on April 28, the platform resumed operations, TRM Labs says.
As eXch’s team earlier said, the project had become the target of a “transatlantic operation” aiming to shut it down and potentially prosecute key figures for money laundering and terrorism. Blockchain analytics firms like Elliptic and others flagged eXch as a key hub in the laundering process.
Following the Feb. 21 theft that drained over 400,000 Ethereum (ETH) from Bybit’s cold wallet, the Lazarus Group used a web of decentralized exchanges, cross-chain bridges, and privacy tools, including eXch, to hide the stolen assets’ origin.